To generate a DKIM (DomainKeys Identified Mail) key with OpenSSL, you can use the following steps:
- Open a terminal window and navigate to the directory where you want to generate the key.
Run the following command to generate a private key:
openssl genrsa -out dkim.key 2048
This will generate a 2048-bit RSA private key and save it to a file called dkim.key.
Run the following command to generate a public key:
openssl rsa -in dkim.key -pubout -out dkim.pub
This will generate a public key based on the private key and save it to a file called dkim.pub.
Run the following command to generate a DKIM DNS record:Copy codecat dkim.pub
This will output the public key to the terminal. You can copy this key and use it to create a DKIM DNS record.
- Add the DKIM DNS record to your domain's DNS records. The record should have a
TXTtype and a name in the format<selector>._domainkey.<domain>, where<selector>is a string you choose to identify the key, and<domain>is your domain name. The value of the record should be the public key you generated in step 3, with thev=DKIM1; p=prefix added.
After following these steps, you should have a private key and a public key that you can use to sign and verify emails using DKIM.
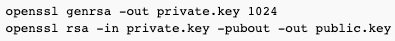
Generating 1024 bit DKIM key
To generate a DKIM key with openssl, do the following - this will generate you a 1024 bit DKIM key:
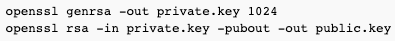
Your generated public key will remind something like below:
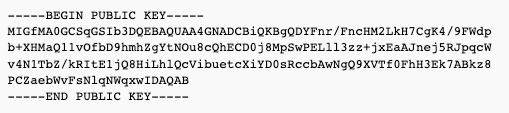
If you need to supply the public.key in the DNS record as follows, you have to "convert" it manually to be in one line, i.e.:
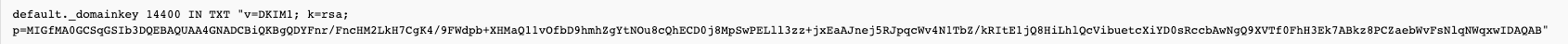
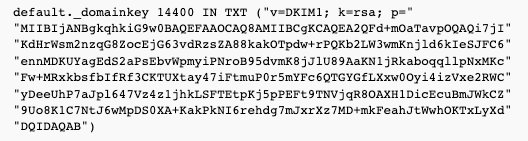
In bind/named compatible format, it will look like below TXT record:
Generating 2048 bit DKIM key
Please note that you may want to use a 2048 bit DKIM key - in this case, use the following openssl commands:
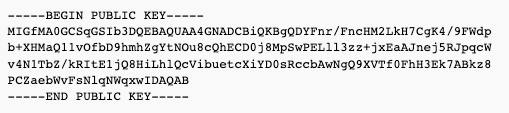
However, 2048 bit public DKIM key is too long to fit into one single TXT record - which can be up to 255 characters. Assuming your full public key is as follows:
...you need to split the text field into parts having 255 characters or less:
There are several limitations to 2048 bit DKIM records:
- While bind/named supports TXT fields being split into several parts, some DNS hostings may still not support it.
- If the total size of the DNS record is larger than 512 bytes, it will be sent over TCP, not UDP. Some buggy firewalls may not permit DNS packets over TCP.
Questions and Snswers About Generating DKIM key with OpenSSL
Q: What is DKIM and why is it used?
A: DKIM (DomainKeys Identified Mail) is a method of email authentication that allows the person receiving the email to check that it was actually sent by the domain it claims to be sent from, and that it hasn't been modified in transit. This helps to prevent email fraud and protect recipients from phishing and other malicious email attacks.
Q: How do I generate a DKIM key using OpenSSL?
A: To generate a DKIM key using OpenSSL, you can use the command openssl genrsa -out private.key 2048 to generate a private key file, and then use openssl rsa -in private.key -out public.key -pubout to extract the public key from the private key file.
Q: What is the purpose of the private key in DKIM?
A: The private key is used to sign the email messages. The signature is then included in the email headers, and can be verified by the receiving mail server using the corresponding public key, which is provided in the DNS records for the domain.
Q: What is the purpose of the public key in DKIM?
A: The public key is used to verify the signature on the email messages. It is provided in the DNS records for the domain, and can be used by the receiving mail server to check that the signature on the email message was created using the corresponding private key.
Q: How do I add the public key to my DNS records?
A: The public key should be added to your DNS records as a TXT record for the domain that the email is being sent from. The format of the record should be "default._domainkey.example.com. IN TXT ( "v=DKIM1; k=rsa; " "p=PUBLIC_KEY" )" where "example.com" is replaced with your domain name and "PUBLIC_KEY" is replaced with the actual public key

