If your internet provider started supporting IPv6 in addition to the usual IPv4, you may want to make sure the new functionality didn't expose your home network to public IPv6 traffic (since your devices, in most cases, will have a public IPv6 address assigned).
Checking if your PC/laptop is exposed to public IPv6 traffic
For example, you can check from some other host in the internet (assuming your public IPv6 address is 2405:6580:3240:0:d755:3717:f0f:176b):


Then, you can run tcpdump to check IPv6 traffic:
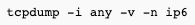
If you see incoming ICMP or SSH packets from the address of the other host in the internet, it means that your PC/laptop is exposed to the public IPv6 internet and anyone out there can connect. While it can be sometimes desired (i.e. public, IPv6-only web server, or just ease of remote access) - in most cases, it's insecure and not wanted.
IPoE, PPPoE, NAT and IPv6
The first thing to do to block incoming IPv6 traffic would be checking your router settings/firewall. Unfortunately, some routers, or some ISP providers will not offer this functionality.
If you have IPv6 IPoE internet - your router may not offer the ability to block incoming IPv6 traffic.
If you have IPv6 PPPoE, most likely your router allows you to add firewall rules.
If your router makes IPv6 NAT, you don't need to do anything, because devices behind the router will not have a public IPv6 address.
Still, please check on your own to make sure.
Blocking incoming IPv6 traffic with ip6tables
Finally, if you've determined that your PC/laptop is publicly available over IPv6 and you'd rather prohibit it, you can use the following ip6tables rules to block the incoming IPv6 traffic. Make sure to modify INTERFACE variable to match your internet-facing interface (i.e. your WLAN or LAN device):
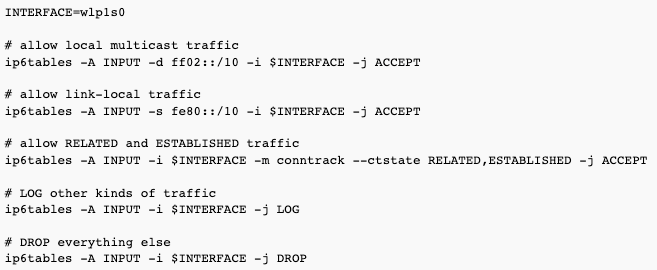
Making it persistent
Once you're sure the rules are working for you, it's best to add them permanently so they persist across reboots.
For example, on Ubuntu or Debian, you can use "iptables-persistent" package to achieve that.

