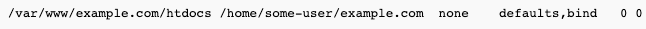To create a SSH user which is only allowed SFTP access (and is not allowed SSH/shell access), add the following to /etc/ssh/sshd_config:
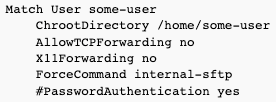
Please note that for this to work, user's home directory must be owned by root - otherwise, sshd will refuse the login.
You may want to uncomment PasswordAuthentication line if you want to use password authentication with this user.
If you need this user for example to edit a web directory, a typical workaround is:
- own user's homedir as root
- mount bind a web directory into user's directory, for example, to /home/some-user/example.com
This is how /etc/fstab entry should look like for a bind mount: